Squirrelwaffle nearly triumphs in Microsoft Exchange Server scam scheme
Squirrelwaffle was just one of the attack methods in a recent campaign to scam an unnamed organization.
What you need to know
- Sophos recently looked into an incident in which Squirrelwaffle malware was spread through an unpatched Microsoft Exchange Server.
- Squirrelwaffle was used together with ProxyLogon and ProxyShell to target the vulnerable server.
- The attack placed infected documents into email threads of targeted employees.
An organization almost fell victim to an attack campaign that used Squirrelwaffle malware together with exploits to ProxyLogon and Proxy Shell to target a Microsoft Exchange Server. Sophos researchers looked into the attack and broke down the methods of the malicious actors that went after the unnamed victim organization.
Despite its funny name, Squirrelwaffle is a dangerous type of malware that is spread through spam campaigns. Attackers hijacked an email thread and replied to messages with what appeared to be innocent attachments. Instead, they were documents that enabled macros to give control of a system to attackers.
A hijacked thread could be quite convincing. For example, a message may claim to be from someone who had been looped into a preexisting thread to share more information. As part of the campaign investigated by Sophos, attackers used a typo-squatted domain that looked similar to the domain a thread began in. This maneuver swapped the thread over to another domain that was less secure.
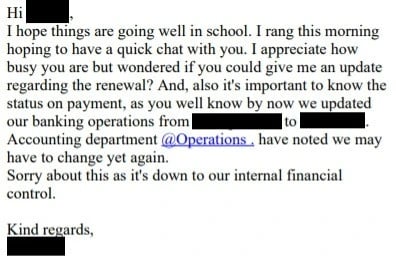
In this specific attack, the threat actors copied in several email addresses to appear legitimate.
"That's very understandable, I shall wait for your updates. Finance department is cc'ed in this email and would provide the updated banking details shortly," said the first message by the attackers.
A later email pressured the victim to make a payment.
The attack was nearly successful. According to Sophos, the unnamed organization transferred money to the attackers, but the payment was flagged up and stopped by a financial institution.
All the latest news, reviews, and guides for Windows and Xbox diehards.
While patching a Microsoft Exchange Server is important, more is needed to secure an organization.
"This is a good reminder that patching alone isn't always enough for protection," said Sophos researcher Matthew Everts to ZDNet. "In the case of vulnerable Exchange servers, for example, you also need to check the attackers haven't left behind a web shell to maintain access. And when it comes to sophisticated social engineering attacks such as those used in email thread hijacking, educating employees about what to look out for and how to report it is critical for detection."
The recently investigated attack was an evolution of previous Squirrelwaffle attacks. In this case, threat actors added the typo-squatting element to the campaign, which made it harder to defend against.

Sean Endicott is a tech journalist at Windows Central, specializing in Windows, Microsoft software, AI, and PCs. He's covered major launches, from Windows 10 and 11 to the rise of AI tools like ChatGPT. Sean's journey began with the Lumia 930, leading to strong ties with app developers. Outside writing, he coaches American football, utilizing Microsoft services to manage his team. He studied broadcast journalism at Nottingham Trent University and is active on X @SeanEndicott_ and Threads @sean_endicott_.