What's new on security for Windows 11 2022 Update
These are the biggest security features available on Windows 11 2022 Update.
Along with the new productivity-focused features, improvements, and visual changes, the Windows 11 2022 Update (version 22H2) also has several enhancements to improve security against ransomware, phishing threats, and sophisticated hacking attacks.
For example, in this release, Microsoft is strengthening security by adding a new Smart App Control (SAC) feature to block dangerous apps. The update enables, by default, features that were previously disabled, such as hypervisor-protected code integrity (HVCI) and vulnerable driver block list.
Also, as part of the SmartScreen technology, version 22H2 enables enhanced phishing protection to warn users when they are typing a password into a compromised app or web service and much more.
This guide highlights the best security that Microsoft is shipping with the Windows 11 2022 Update.
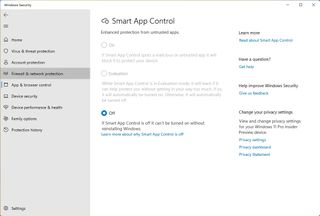
Smart App Control
On the Windows 11 2022 Update, Smart App Control (SAC) is a new security feature in the Windows Security app that helps to prevent scripting attacks and protect you from running untrusted or unsigned apps that may be associated with malware or attack tools. The feature accomplishes this by using an AI model that proactively receives updates to predict and decide if the app is safe to use.
The app is available for all the editions of Windows 11 with a clean installation of version 22H2, but network administrators can also use Microsoft Intune to set it up.
You first need to enable Smart App Control in evaluation mode. In this mode, the feature will learn and determine if it can help protect the computer without being intrusive. If this is the case, SAC will automatically enable itself. Otherwise, it will automatically disable itself.
Get the Windows Central Newsletter
All the latest news, reviews, and guides for Windows and Xbox diehards.
Vulnerable driver protection
Starting on Windows 11 version 22H2, the system uses virtualization-based security (VBS) to improve kernel protection to help prevent driver vulnerability exploits on the latest silicon from AMD, Intel, and Qualcomm.
As part of these changes, the memory integrity (hypervisor-protected code integrity (HVCI)) feature will now be enabled by default on new devices.
According to the company, the memory integrity feature uses VBS to run kernel mode code integrity (KMCI) inside the secure environment instead of the kernel to minimize attacks that attempt to modify the kernel. In other words, using this approach, only validated code will be executed in kernel mode.
Microsoft is also implementing a list of vulnerable drivers to block specific drivers from loading to prevent persistent threats and ransomware attacks from exploiting known vulnerable drivers to access the Windows kernel.
The block policy now comes enabled by default, but users need to enforce it manually through the Windows Defender Application Control.
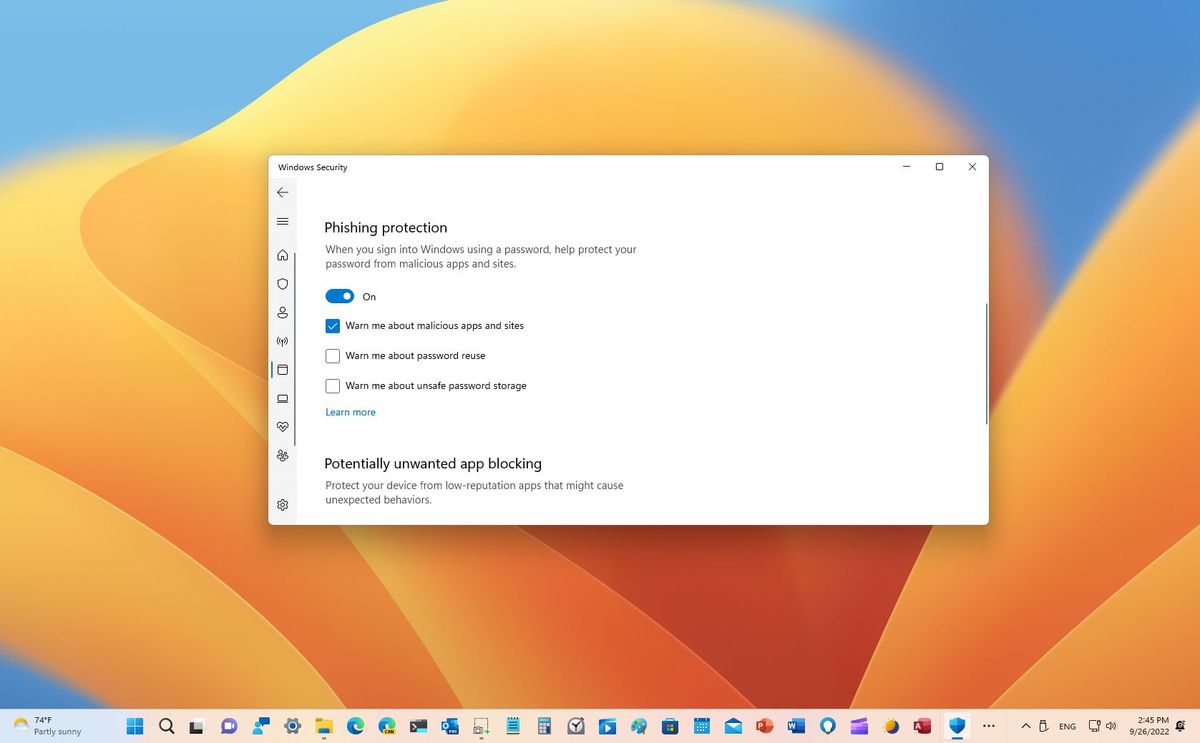
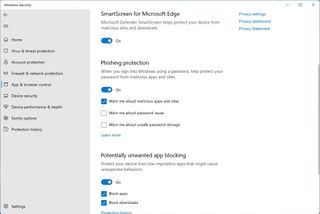
Enhanced phishing protection
The 2022 Update also brings "enhanced phishing protection" as part of the SmartScreen technology that can determine in real-time whether the web service or application is secure and a trusted entity. If not, Windows 11 will detect that the user is trying to type a password and let them know the risk. According to the company, this will allow network administrators to identify when a password has been compromised and take the necessary actions.
The new protection works with Microsoft Account, Active Directory, Azure Active Directory, local passwords, and on any Chromium-based browser (such as Microsoft Edge and Google Chrome) or any application that may connect to a phishing site.
When a new phishing attack is detected, the end user will get a dialog notification and suggest changing the password. Also, the problem will then be submitted to the technology department using the MDE portal.
Furthermore, the anti-phishing feature will warn users about reusing their passwords and if they try to store other passwords on the computer using any note-taking application like Notepad.
Personal Data Encryption (PDE)
Windows 11 version 22H2 also comes with Personal Data Encryption (PDE), a new security feature in the Enterprise edition of the operating system that provides more ways of data encryption.
While BitLocker uses encryption for the entire drive, PDE offers encryption for individual files using Windows Hello for Business to link the encryption keys with the user credentials for quick decryption.
In the event that the device is misplaced, the attacker will have to bypass the already strong protection of BitLocker, but only to find out that individual files are also encrypted using PDE, creating a second layer of protection.
Other security improvements
For businesses and organizations, Microsoft is also enabling several features by default and softening the requirements for others to help improve the security of Windows 11.
In this release, for example, Windows Defender Credential Guard now comes enabled by default to minimize attacks against credential theft techniques, such as pass-the-hash or pass-the-ticket.
Microsoft is also enabling the Credential isolation with Local Security Authority (LSA) protection by default on version 22H2 to add an extra layer of protection for domain-joined devices since this is an important process to verify a user's identity.
In addition, the company is making deploying Windows Hello for Business easier by removing the need for public key infrastructure (PKI) to set up the feature.
Finally, there's a new feature known as "Config lock" for "Secured-core PCs." The feature has been designed to prevent misconfigurations when users with administrator privileges make system changes, putting the computer out of sync with the company's security policies. When using this feature, if the system detects unwanted changes, it will revert immediately to the original settings previously configured by the organization.
More resources
For more helpful articles, coverage, and answers to common questions about Windows 10 and Windows 11, visit the following resources:
Mauro Huculak has been a Windows How-To Expert contributor for WindowsCentral.com for nearly a decade and has over 15 years of experience writing comprehensive guides. He also has an IT background and has achieved different professional certifications from Microsoft, Cisco, VMware, and CompTIA. He has been recognized as a Microsoft MVP for many years.
