This malicious Microsoft Teams phishing scam pretends to be harmless vacation changes
Beware: Don't open any unusual 'changes to the vacation schedule' attachments.
What you need to know
- Hackers are leveraging a new phishing campaign dubbed 'DarkGate Loader' to compromise Microsoft Teams accounts.
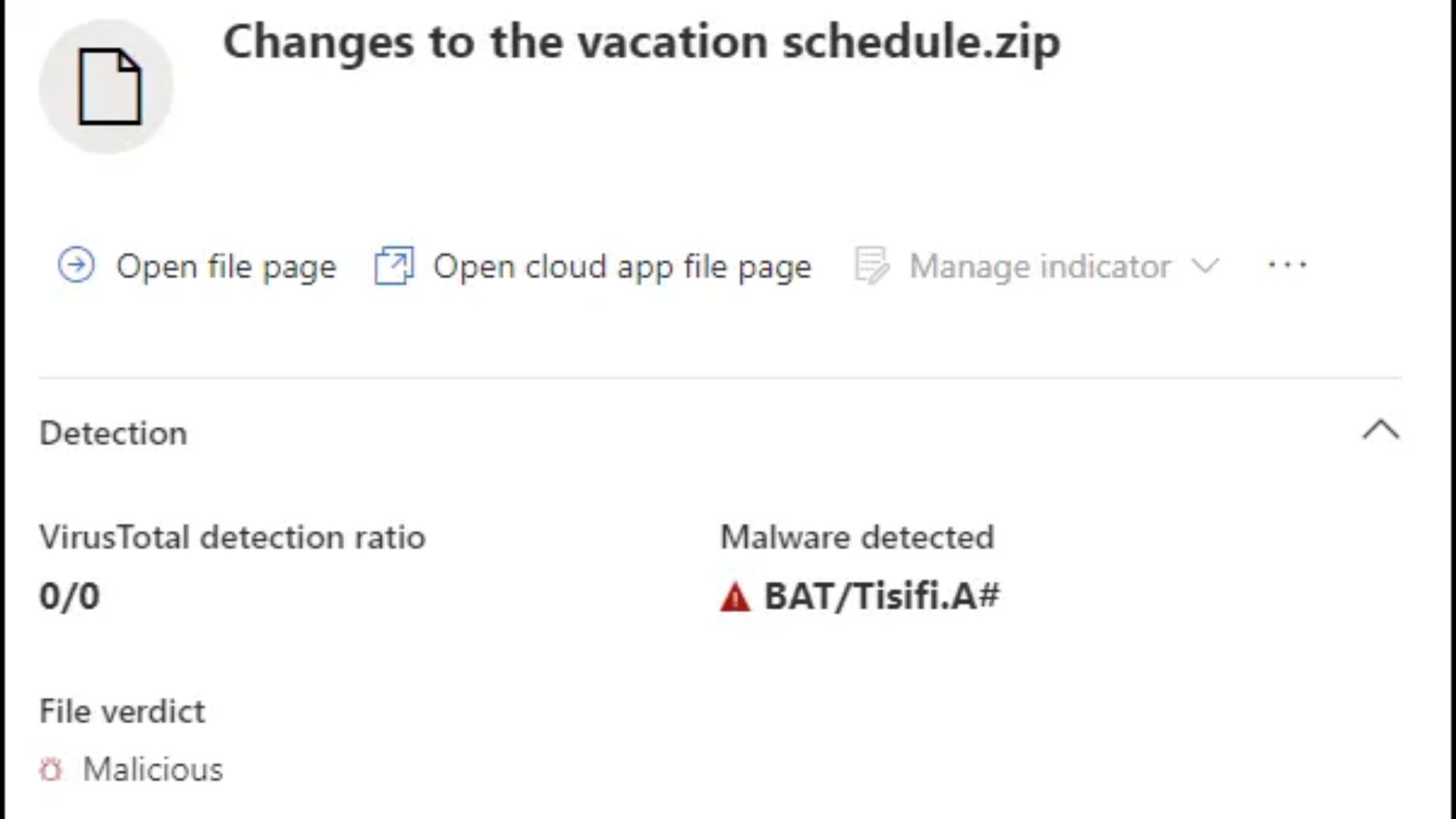
- The technique is designed to dupe unsuspecting users into downloading and opening .ZIP files marked 'Changes to the vacation schedule' onto their devices.
- The disguised download process uses Windows cURL, and the pre-compiled script makes it harder to spot the malware since the code is hidden.
Hackers are leveraging sophisticated techniques to dupe and lure unsuspecting users into their malicious attacks. Toward the end of August, Truesec's research team started investigating a new process dubbed 'DarkGate Loader.'
This phishing campaign sends seemingly harmless messages to Microsoft Teams users. The hackers used compromised Office 365 accounts to send messages with harmful attachments to unsuspecting users to trick them into downloading and opening ZIP files marked 'Changes to the vacation schedule.'
Be aware that clicking on this ZIP file automatically initiates a download process from a SharePoint URL containing an LNK file disguised as a PDF document (via TechRadar.)
Trusec highlighted the hijacked accounts used by the hackers: "Akkaravit Tattamanas" (63090101@my.buu.ac.th) and "ABNER DAVID RIVERA ROJAS" (adriverar@unadvirtual.edu.co), sending malicious VBScript lurking inside the LNK file which in turn deploys the malware known as DarkGate Loader.
The sophisticated campaign leveraged by the hackers makes it extremely difficult for users to detect foul play since the download process of the ZIP files makes use of a SharePoint URL. Moreover, the pre-compiled script makes it harder to detect the malware since the code is hidden in the middle of the file.
According to the research firm, the script can also identify whether the target user has Sophos, a popular antivirus, installed on their endpoinIfhat it's not installed, the additional code is unmasked, and shellcode is launched, which leverages a technique dubbed 'stacked strings' to construct the DarkGate executable and load it in the system memory.
This attack was detected due to the security awareness training of the recipients. Unfortunately, current Microsoft Teams security features such as Safe Attachments or Safe Links was not able to detect or block this attack. Right now, the only way to prevent this attack vector within Microsoft Teams is to only allow Microsoft Teams chat requests from specific external domains, albeit it might have business implications since all trusted external domains need to be whitelisted by an IT administrator.
Trusec Research Team
It's not the only Teams-related scam, as a group of Russian hackers named Midnight Blizzard recently leveraged a new exploit that affected under 40 organizations in August. The hackers used previously compromised Microsoft 365 tenants belonging to small business owners to create new domains that purport to be technical support entities. However, Microsoft has since mitigated the issue and is currently investigating the attack's impact.
All the latest news, reviews, and guides for Windows and Xbox diehards.
For now, you should remain vigilant to unexpected messages and alert your administrator if you identify this infected file.

Kevin Okemwa is a seasoned tech journalist based in Nairobi, Kenya with lots of experience covering the latest trends and developments in the industry at Windows Central. With a passion for innovation and a keen eye for detail, he has written for leading publications such as OnMSFT, MakeUseOf, and Windows Report, providing insightful analysis and breaking news on everything revolving around the Microsoft ecosystem. While AFK and not busy following the ever-emerging trends in tech, you can find him exploring the world or listening to music.