Phishing has evolved: Microsoft exposes a new campaign's malicious trickery
Get Microsoft's security outlook on phishing and Outlook.
What you need to know
- The Microsoft 365 Defender Threat Intelligence Team (what a name!) has published another report on security threats Windows users should be aware of.
- This time around, the findings relate to advancements in the phishing space.
- Microsoft's security team has identified a new phishing campaign with a novel twist that involves "joining an attacker-operated device to an organization's network."
Everytime security teams and the general public get wise to a phishing scheme's tricks and traps, it falls on the schemers to cook up a more elaborate twist on the formula to keep the swindle going. Enter: The latest evolution of phishing, as reported by Microsoft.
The Microsoft 365 Defender Threat Intelligence Team has a hefty security blog post analyzing a multi-phase phishing campaign that packs a fresh danger in the form of binding an attacker-operated gadget to the network of an organization it wants to get inside, thereby enabling speedy lateral expansion of the campaign's target pool.
"The first campaign phase involved stealing credentials in target organizations located predominantly in Australia, Singapore, Indonesia, and Thailand," Microsoft's report says. "Stolen credentials were then leveraged in the second phase, in which attackers used compromised accounts to expand their foothold within the organization via lateral phishing as well as beyond the network via outbound spam."
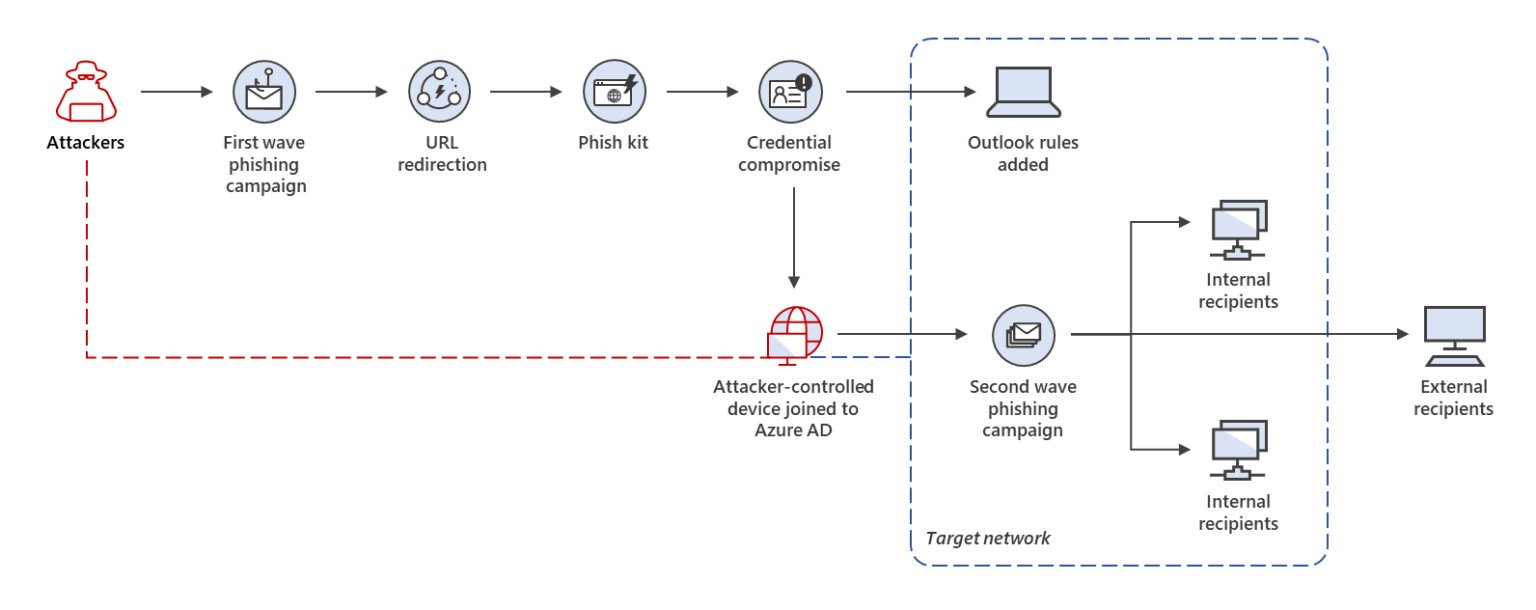
Phase two of the aforementioned campaign can be combated with multifactor authentication (MFA). Organizations without MFA enabled, however, were susceptible to the lateral spread of credential theft and criminal maleficence. And don't assume all organizations have MFA enabled, because that'd be far from accurate. For example, plenty of organizations with Microsoft 365 fail to use its security tools, even though they're actively paying for them.
In its technical breakdown of how the phishing campaign phases are carried out, Microsoft examines a situation wherein Outlook is used to facilitate the spread. Once an attacker gets into a user's account, the mailbox gets abused, and it's all downhill from there. It's worth reading Microsoft's post if you want all the technical details behind what the attackers are up to.
Get the Windows Central Newsletter
All the latest news, reviews, and guides for Windows and Xbox diehards.
Robert Carnevale is the News Editor for Windows Central. He's a big fan of Kinect (it lives on in his heart), Sonic the Hedgehog, and the legendary intersection of those two titans, Sonic Free Riders. He is the author of Cold War 2395. Have a useful tip? Send it to robert.carnevale@futurenet.com.

