Microsoft says 80% of identified SolarWinds attack victims are in the US
Government agencies, security firms, technology firms, and more are targets of the SolarWinds supply chain attack.

What you need to know
- Microsoft identified over 40 of its customers that have been targeted by the SolarWinds supply chain attack.
- More than 80 percent of the identified victims were located in the United States.
- The attack targeted government agencies, security firms, technology firms, government contractors, and more.
Microsoft identified over 40 of its customers that have been targeted by the recent cyberattack that utilized the SolarWinds Orion platform (via ZDNet). Microsoft discovered this information with data from Microsoft Defender. The attacks surfaced last week after security firm FireEye stated that state-sponsored hacking groups used a malware-laced version of SolarWinds Orion, which is a popular network monitor tool for enterprises. SolarWinds shared a press release on the Cyber Attack.
The attacks targeted government agencies and went after security firms, technology firms, government contractors, and more.
SolarWinds explains that the "attack was very sophisticated supply chain attack, which refers to a disruption in a standard process resulting in a compromised result with a goal of being able to attack subsequent users of the software." According to SolarWinds, around 18,000 customers installed trojanized updates.
Microsoft president, Brad Smith, outlines the attack and its far-reaching effects in great detail in a blog post. Smith highlights that "This is not 'espionage as usual,' even in the digital age. Instead, it represents an act of recklessness that created a serious technological vulnerability for the United States and the world."
Microsoft took several steps this week to protect customers, including seizing the web domain that was used to report information to cyberattackers. Microsoft worked with GoDaddy and FireEye to turn the domain into a kill switch to prevent malware from reporting back and downloading a second-stage payload for attacks.
Reuters initially reported that hackers utilized the attacks to access Microsoft's internal network, but Microsoft issued a statement denying that the attacks were able to access production services or customer data:
Like other SolarWinds customers, we have been actively looking for indicators of this actor and can confirm that we detected malicious SolarWinds binaries in our environment, which we isolated and removed. We have not found evidence of access to production services or customer data. Our investigations, which are ongoing, have found absolutely no indications that our systems were used to attack others (emphasis added).
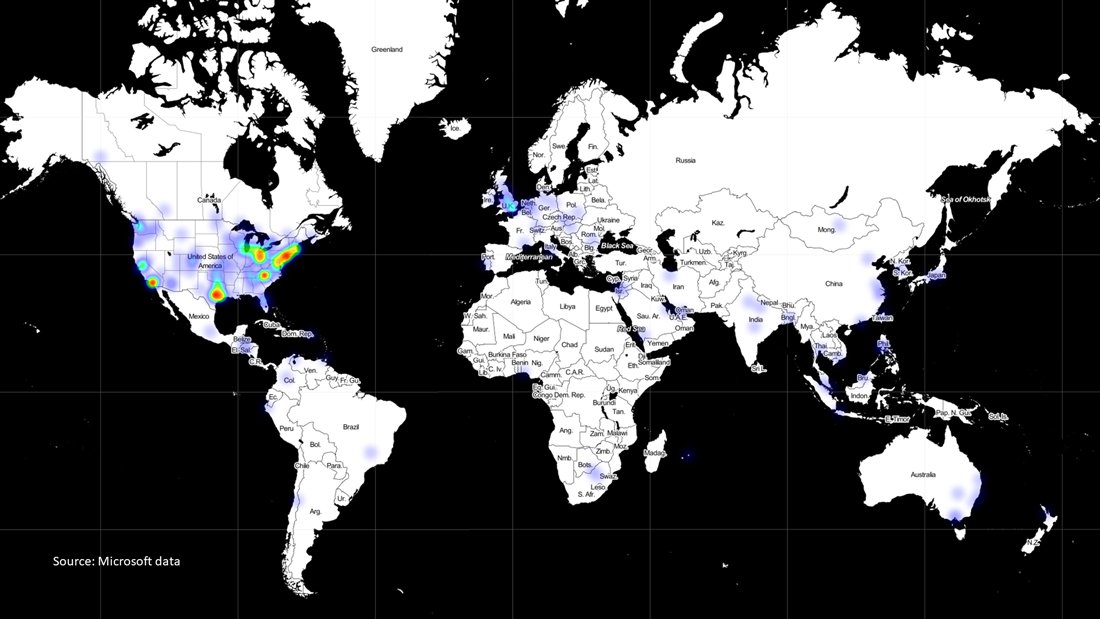
Microsoft identified over 40 of its customers targeted by the attack that have been compromised through "additional and sophisticated measures." Microsoft is working to notify these customers. According to Microsoft, roughly 80 percent of the targeted customers are in the United States, but there are also victims in seven other countries; Canada, Mexico, Belgium, Spain, the United Kingdom, Israel, and the UAE. Smith states that "It's certain that the number and location of victims will keep growing."
All the latest news, reviews, and guides for Windows and Xbox diehards.
"We are witnessing an attack by a nation with top-tier offensive capabilities," said FireEye CEO Kevin Mandia in a blog post on the attacks.
Microsoft states that "The attack is ongoing and is being actively investigated and addressed by cybersecurity teams in the public and private sectors, including Microsoft."

Sean Endicott is a news writer and apps editor for Windows Central with 11+ years of experience. A Nottingham Trent journalism graduate, Sean has covered the industry’s arc from the Lumia era to the launch of Windows 11 and generative AI. Having started at Thrifter, he uses his expertise in price tracking to help readers find genuine hardware value.
Beyond tech news, Sean is a UK sports media pioneer. In 2017, he became one of the first to stream via smartphone and is an expert in AP Capture systems. A tech-forward coach, he was named 2024 BAFA Youth Coach of the Year. He is focused on using technology—from AI to Clipchamp—to gain a practical edge.
