Microsoft patches major Cortana lock screen bypass bug in Windows 10
Attackers with access to your PC could use Cortana to execute commands with elevated privileges.

Microsoft this week patched a major Cortana bug that could allow attackers to execute commands from the lock screen. The bug was originally discovered by McAfee researchers, who say they disclosed details of the issue to Microsoft on April 23 (via Windows Latest).
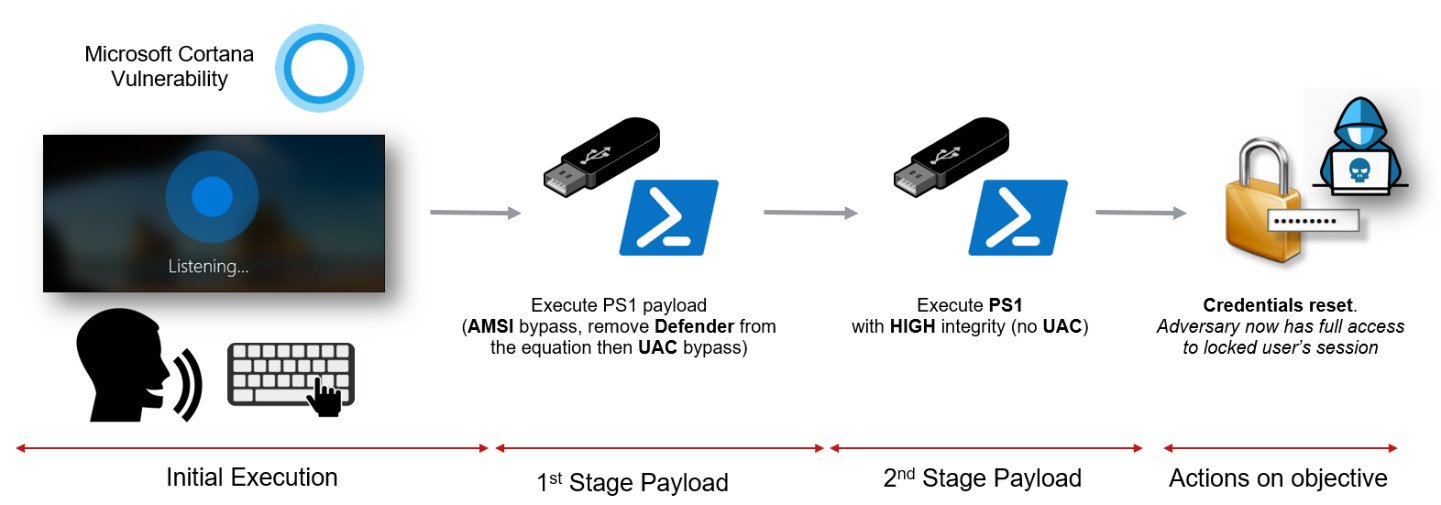
The vulnerability can be exploited via a number of methods, but they all have one commonality: an attacker requires physical access to your PC. If executed correctly, hackers could use Cortana from the lock screen to run PowerShell scripts or load malicious software from a USB stick. Researchers were also able to use the exploit to perform a password reset and gain full access to the machine.
Microsoft this week shipped a fix for the vulnerability with its latest Patch Tuesday updates for June. Further, according to Microsoft's security guidance, the issue is limited to PCs and server core installations running the Windows 10 Fall Creators Update and April 2018 Update.
Still, if you haven't yet installed the Patch Tuesday updates for June, or are planning to hold off, the best mitigation for the vulnerability is to disable Cortana on the lock screen.
All the latest news, reviews, and guides for Windows and Xbox diehards.

Dan Thorp-Lancaster is the former Editor-in-Chief of Windows Central. He began working with Windows Central, Android Central, and iMore as a news writer in 2014 and is obsessed with tech of all sorts. You can follow Dan on Twitter @DthorpL and Instagram @heyitsdtl.
