How to check if your PC is protected from the Meltdown and Spectre exploits
Here are the steps to determine if your Windows 10 PC is still vulnerable to the Meltdown and Spectre exploits, and we'll also tell you what to do if you're not protected.
A number of security researchers have recently disclosed two vulnerabilities ("Meltdown" and "Spectre") found in many modern processors. These are major hardware design flaws that attackers can exploit to access part of the memory that should remain private allowing them to steal your information (passwords, emails, browser history, and photos).
These flaws affect a large number of processors released in the past two decades, including those manufactured by Intel, Advanced Micro Devices (AMD), and ARM — but it's still primarily an Intel problem. AMD has published a statement clarifying that one (branch target injection) of the two Spectre variants doesn't impact its processors, and the second variant (bounds check bypass) can be resolved through a software update. The third variant, Meltdown (rogue data cache load), doesn't impact AMD chips either due to architecture differences.
In addition, as a result of these two now famous security flaws, supported OSes, such as Windows 10, macOS, Linux, as well as many other pieces of software, are also compromised.
Microsoft has already released a patch to mitigate part of the problem on Windows 10, and now hardware manufacturers are starting to roll out firmware updates to address the other part. However, because this is a multi-step solution to properly (but not entirely) fix the problem, it can be difficult to tell if your PC has been immunized, which is why the software giant also created a PowerShell script to check if your device is still vulnerable.
In this Windows 10 guide, we'll walk you through the steps to check if your device has the required system and firmware updates to mitigate the latest microprocessor security vulnerabilities. In addition, we'll look at the steps you need to follow if your computer is still not protected.
- How to check if your PC is protected against CPU vulnerabilities
- How to protect your PC from CPU vulnerabilities
How to check if your PC is protected against CPU vulnerabilities
In order to verify that you're protected against the latest microprocessor security vulnerabilities, you can use a PowerShell script created by Microsoft:
- Open Start.
- Search for Windows PowerShell, right-click the top result, and select Run as administrator.
- Type the following command to install the required module and press Enter:
Install-Module SpeculationControl
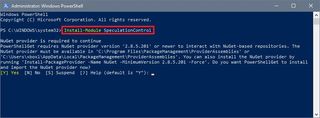
- Type Y and press Enter if you're prompted to enable NuGet provider.
- Type Y and press Enter if you're prompted to confirm the installation from an untrusted repository.
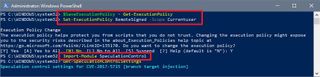
- Type the following command to save the current execution policy so it can be reset and press Enter:
$SaveExecutionPolicy = Get-ExecutionPolicy - Type the following command to ensure you can import the module in the next step and press Enter:
Set-ExecutionPolicy RemoteSigned -Scope Currentuser - Type Y when prompted to confirm the execution policy change and press Enter:
- Type the following command and press Enter:
Import-Module SpeculationControl
- Type the following command to check if your device has the necessary updates and press Enter:
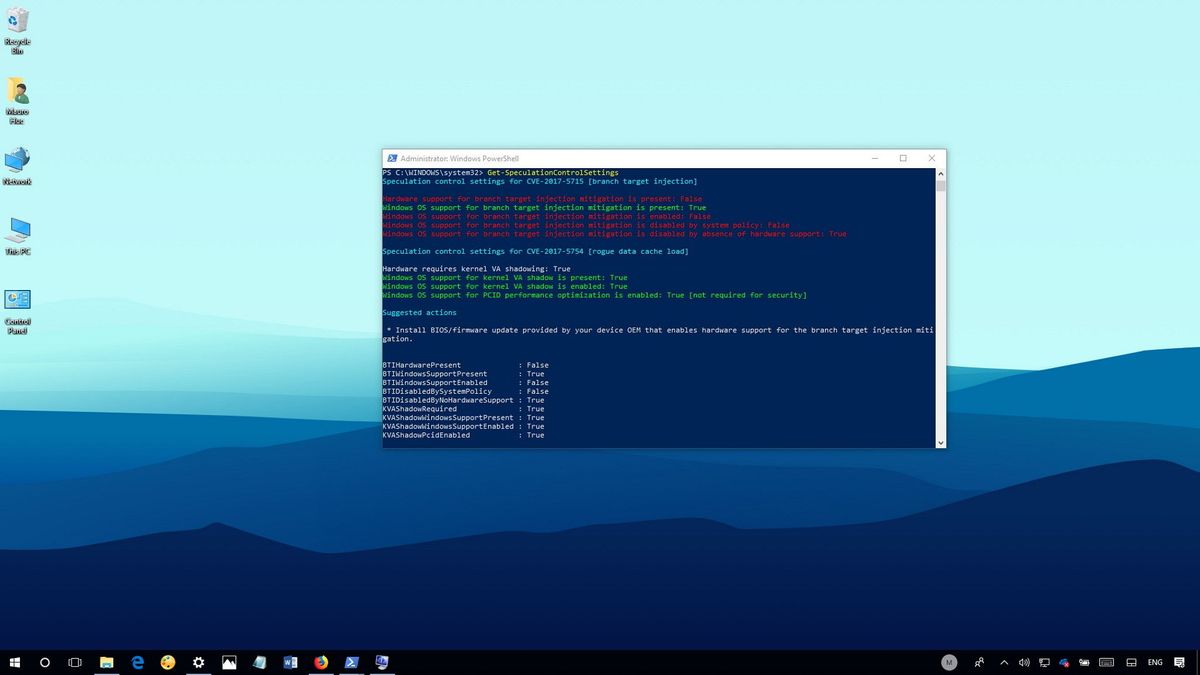
Get-SpeculationControlSettings
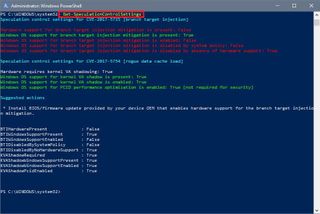
Once you completed these steps, you'll be able to determine whether or not your computer is still vulnerable to the Meltdown and Spectre security flaws.
Get the Windows Central Newsletter
All the latest news, reviews, and guides for Windows and Xbox diehards.
If your machine only has the emergency patch for Windows 10 installed, which only addresses the Meltdown vulnerability, then you'll see all the requirements for "rogue data cache load" (Meltdown) set to True and highlighted in green.
Also, under the "branch target injection" (Spectre) only the software mitigation is present and set to True, but it won't show up as enabled if your device doesn't have the latest Basic Input/Output System (BIOS) or Unified Extensible Firmware Interface (UEFI) update from your hardware manufacturer.
Only after installing the emergency Windows 10 update and the required version of the BIOS or UEFI update will all the requirements under "branch target injection" and "rogue data cache load" be set to True and highlighted in green, indicating that your device is protected.
After you're done verifying the state of your device, type the following PowerShell command
Set-ExecutionPolicy $SaveExecutionPolicy -Scope Currentuserto roll back the execution policy to the original state and press Enter, and then type Y and press Enter to confirm the reset.
How to protect your PC from CPU vulnerabilities
Windows Update
The update that helps to mitigate the security vulnerabilities should install automatically, but if after running the PowerShell script, you notice that your device isn't protected, there could be a problem with Windows Update or there could be an antivirus conflict.
While creating the latest patch for Windows 10, Microsoft found that some antivirus solutions may cause a Blue Screen of Death (BSOD) that will prevent a device from starting. As a result, if you're running an unsupported third-party antivirus, Windows Update won't download and install the mitigation for the vulnerability.
If your computer isn't getting the update, visit your antivirus company's support website to find out if a new software update is available and follow thr instructions to apply it.
In the case that the antivirus doesn't have the patch to address the compatibility issue with Windows 10; you can temporarily uninstall the third-party antivirus. (Although, it's not recommended to keep your computer unprotected, remember that as you uninstall the third-party malware solution Windows Defender Antivirus will enable automatically.)
Uninstalling security software should be a straightforward process, but it's always a good idea to check your software company support website for specific instructions before using the steps below:
- Open Settings.
- Click on Apps.
- Click on Apps & features.
- Select the antivirus.
- Click the Uninstall button.
- Click the Uninstall button again.
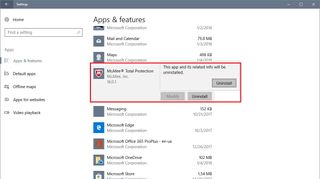
- Continue with the on-screen directions to remove the antivirus.
If you have a problem with Windows Update, use the troubleshooter to fix the issue:
- Open Settings.
- Click on Update & Security.
- Click on Troubleshoot.
- Under "Get up and running," select Windows Update.
- Click the Run the troubleshooter button.
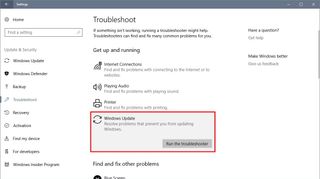
- Continue with the on-screen directions to fix Windows Update.
After installing the antivirus software update, or fixing Windows Update, use these steps to install the mitigation:
- Open Settings.
- Click on Update & Security.
- Click on Windows Update.
- Click the Check for updates button.
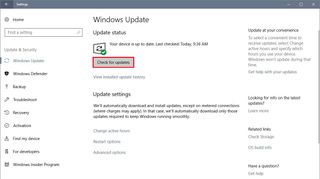
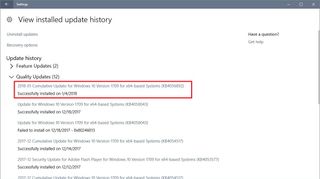
After the update downloads and installs, return to the Windows Update settings page, click the View installed update history link, and verify that one of the following updates has been successfully applied on your device:
- KB4056892 — Windows 10 version 1709 (Fall Creators Update).
- KB4056891 — Windows 10 version 1703 (Creators Update).
- KB4056890 — Windows 10 version 1607 (Anniversary Update).
- KB4056888 — Windows 10 version 1511 (November Update).
- KB4056893 — Windows 10 version 1507 (Initial Release).
BIOS/UEFI update
In order to patch the Spectre vulnerability, a BIOS or UEFI update is required to be applied to your computer. Depending on the brand and model of your device the steps to install the latest firmware update will be different, as such make sure to visit your manufacturer support website to check for the latest update and the specific instructions on how to apply it.
You can use the links in the list below to check your device manufacturer support website for the latest firmware update to mitigate these new vulnerabilities. (If the manufacturer isn't in the list, you may need to contact the company directly.)
| OEM Device Manufacturers | Link to firmware availability |
|---|---|
| Acer | https://www.acer.com/ac/en/US/content/support |
| Asus | https://www.asus.com/News/YQ3Cr4OYKdZTwnQK |
| Dell | https://www.dell.com/support/meltdown-spectre |
| Fujitsu | https://www.fujitsu.com/global/support/products/software/security/products-f/jvn-93823979e.html |
| HP | https://support.hp.com/ca-en/document/c05869091 |
| Lenovo | https://support.lenovo.com/us/en/solutions/len-18282 |
| LG | https://www.lg.com/us/support |
| Panasonic | https://pc-dl.panasonic.co.jp/itn/vuln/g18-001.html |
| Samsung | https://www.samsung.com/us/support/ |
| Toshiba | https://support.dynabook.com/ |
| Vaio | https://vaio.com/support/ |
If you have a Surface device, Microsoft has already made available a firmware update to help mitigate these vulnerabilities on Windows 10 version 1709 (Fall Creators Update) and version 1703 (Creators Update) for the following devices:
- Surface Pro 3.
- Surface Pro 4.
- Surface Book.
- Surface Studio.
- Surface Pro Model 1796.
- Surface Laptop.
- Surface Pro with LTE Advanced.
- Surface Book 2.
Surface devices should receive the latest firmware update automatically, but you can can always force the update from Settings > Update & Security > Windows Update, and clicking the Check for updates button.
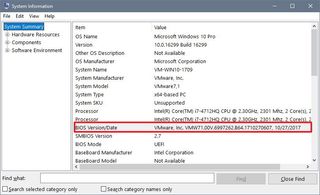
In order to check if you're running the latest BIOS or UEFI update use the following steps:
- Open Start.
- Search for msinfo32 (or System Information) and press Enter.
- On "Summary," check the BIOS Version\Date information.
Software update
Alongside applying the Windows 10 emergency patch and the latest firmware update to stay protected against the Meltdown and Spectre vulnerabilities, you also want to ensure to check for app updates (especially for your web browser, as it's possible to use similar techniques to compromise your information when surfing the internet).
Microsoft has already patched the latest version of Internet Explorer and Microsoft Edge. Mozilla protects Firefox users against these particular exploits starting with version 57. And Google is expected to release a Chrome update on January 23, which will also include Site Isolation enabled by default to add an extra layer of security.
Wrapping things up
Running the latest updates, in some cases, doesn't necessarily mean that you're automatically protected. After taking care of all the patches, use the PowerShell script again to make sure that your PC is no longer vulnerable.
Although many companies like Microsoft are quickly responding to mitigate the security issues with Meltdown and Spectre, keep in mind that these are just the first wave of updates. In the near future we're expected to see additional updates to better address these problems. However, these are complicated flaws that will ultimately require to replace the processor to fix these vulnerabilities permanently.
More Windows 10 resources
For more helpful articles, coverage, and answers to common questions about Windows 10, visit the following resources:
- Windows 10 on Windows Central – All you need to know
- Windows 10 help, tips, and tricks
- Windows 10 forums on Windows Central
Mauro Huculak has been a Windows How-To Expert contributor for WindowsCentral.com for nearly a decade and has over 15 years of experience writing comprehensive guides. He also has an IT background and has achieved different professional certifications from Microsoft, Cisco, VMware, and CompTIA. He has been recognized as a Microsoft MVP for many years.
