Decryption tool now available for some strains of the Petya ransomware
Some relief is now available for victims of at least some strains of the Petya ransomware.
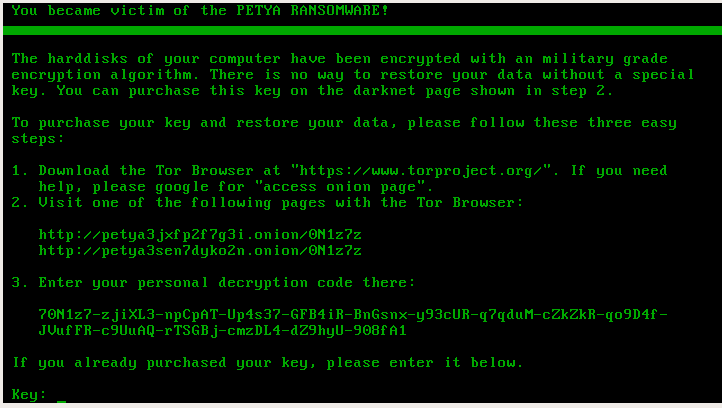
A new decryption tool is now freely available to help people impacted by some strains of the Petya ransomware recover their files. Recently released by Malwarebytes (via ZDNet), the tool unfortunately doesn't work on PCs infected with the recent Petya/NotPetya outbreak that spawned from Ukraine in June and spread around the globe. It does, however, work on earlier iterations of the malware.
Following the launch of the recent Ukraine attack, the author of the original Petya malware (it's had several iterations) released his master key. Malwarebytes explains that it was able to use that key to build a decryption tool that unlocks the following three variants of the malware:
- Red Petya
- Green Petya (both versions) + Mischa
- Goldeneye (bootlocker + files)
Identifying which strain a PC has been hit with is fairly simple. Each of the three will display the ransom screen in the color that it is named after. In other words, Red Petya will display a red background, Green Petya has green text on a black background, and Goldeneye shows gold text on a black background. If you use the tool, keep in mind that Malwarebytes notes it saw some instances of Petya hanging during decryption or damaging data via other issues. The firm recommends making a backup of the drive before attempting to use the tool.
While the tool doesn't work on the most recent version of Petya that rocked Ukraine, that attack's reach was more limited than it could have been. Microsoft in its own post-attack analysis stated that the attack "had far less reach than we expected given its worm-like spreading capabilities." Most infections were found in Windows 7 machines, and more than 70 percent of infected PCs were in Ukraine, the company explained. The concentrated nature of the spread led some to speculate that it was a state-sponsored attack targeted at Ukrainian digital infrastructure.
For more, you can download the tool and follow detailed instructions for using it at Malwarebytes.
Get the Windows Central Newsletter
All the latest news, reviews, and guides for Windows and Xbox diehards.
Dan Thorp-Lancaster is the former Editor-in-Chief of Windows Central. He began working with Windows Central, Android Central, and iMore as a news writer in 2014 and is obsessed with tech of all sorts. You can follow Dan on Twitter @DthorpL and Instagram @heyitsdtl.

