Ambient computing puts us at greater risk from hackers
As personal computing becomes increasingly ambient - distributed across many devices around us - opportunities for hackers become more pervasive.

We all love the conveniences of modern technology. Washing machines, vacuum cleaners, automobiles and more help us save time and diminish the burden of many of life's duties. Using a bathroom is far more convenient than marching several yards from a house to relieve oneself in an outhouse. And dropping laundry into a machine, adding soap and pushing a button is much easier than spending hours at the bank of a river forcing dirt and stains from one's clothes.
Speaking into the air to buy a product via Amazon Echo, unlocking a car door with an app or controlling blinds, cameras and thermostats with a phone are also convenient. These experiences are some of the early examples of ambient computing.
Unfortunately, the connected nature of ambient computing brings with its comforts a vulnerability to external threats. As we embrace connected technology, we're also embracing the tapestry that connects it - the internet - along with its inherent vulnerabilities. As our homes and vehicles become just as connected as our phones and PCs, compromises of our devices can range from access to our data to the endangering our lives.
Hacking our smartphones

Smartphones have arguably become the most personal devices we carry. As the portal to a host of social media accounts, banking information, private photos, conversations and more they contain the passwords and credentials to our digital lives. We trust much of that data to the cloud, which is simply computer hardware maintained and supervised in a remote location by an entity, such as Microsoft, Google or some other company. That data is hackable.
If our phones are hacked our other devices are vulnerable.
Our smartphones are also the hub for emerging technologies such digital assistants, smart homes, connected cars and more. If our phones are hacked not only is local data on the device compromised, but everything the phone connects to is also vulnerable.
Hackers have shown how malware posing as legitimate apps or OS vulnerabilities can be used to hack smartphones. Phone numbers, credit card information, social media accounts, SMS and even smartphone cameras and microphones were fair game for the hackers. Victims of these hacks have no idea their cellphone cameras have remotely taken pictures or recorded video of them.
How Microsoft's mixed realty strategy may augment its Home Hub and IoT visions
All the latest news, reviews, and guides for Windows and Xbox diehards.
Facing the truth about facial recognition
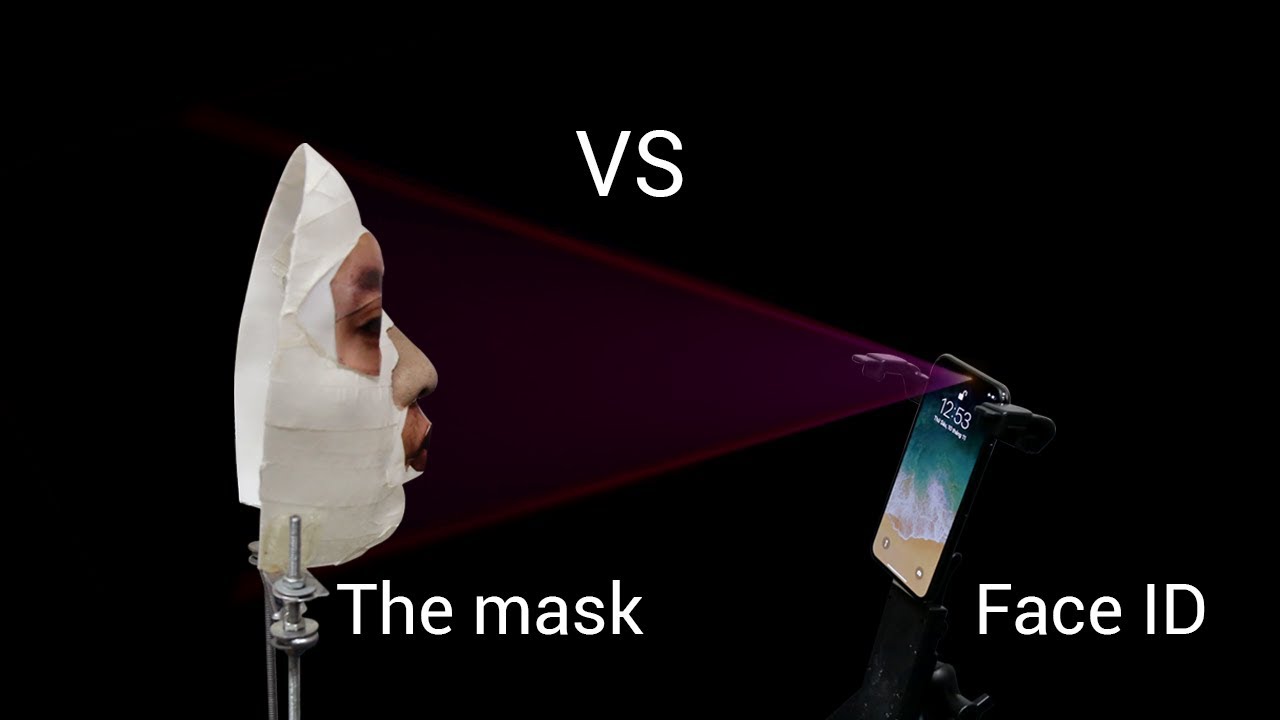
Biometric security such as Apple's iPhone X's facial recognition has also apparently proven less reliable than promised. Vietnamese security firm Bkav created a mask that reportedly fooled the much-touted system as seen in the above video.
iPhone X's facial recognition isn't a foolproof security system.
In much less sophisticated scenarios non-twin brother's reportedly confused the system. One of those cases has since been explained while the other still stands as troubling evidence of the system's vulnerability. These both fall under the umbrella of "spoofing" — the process of fooling a security system like facial recognition or fingerprint scanners. Given an accurate enough replica of a key, you can open a lock.
This proves that despite our best attempts nothing's impervious. Consequently, as we trust more of our data, our homes and our vehicles to the internet, we must be aware of the potential vulnerabilities we expose ourselves to.
Hacking smart homes through Wi-Fi
Smart homes are becoming increasingly popular. Wi-Fi and the internet connect locks, blinds, thermostats, security cameras, televisions, appliances and more to users mobile devices. Being able to control aspects of or see within one's home remotely has its benefits. It also has its detriments when that access falls into the hands of hackers.
In the above video, hackers demonstrate how easy it is to connect to a homeowners Wi-Fi to gain control of connected cameras, TV's, lights and more. They also noted that everyone visiting the home, that connected their phones to the Wi-Fi had also become vulnerable.
Additionally, the Amazon's Echo smart speaker (2015/2016 models) have proven susceptible to a physical hack. And it seems that it's just a matter of time before a hack of Amazon's new delivery service which allows a specially designed lock to be remotely disengaged to enable access to a home becomes news. Such a hack could be life-threatening.
Hacking connected cars
Car manufacturers are competing to integrate internet-connected cellular services for safety, entertainment, and navigation into their vehicles. The car's computer, which is connected to the engine, locks, transmission, steering system and more is therefore accessible over the internet. This is good for when these things are accessed to help owners. But as hackers Charlie Miller and Chris Valasek proved, certain vehicles could be hacked both from within the car and remotely potentially giving control of one's car to someone with ill intent.
Via an internet connection, they could see connected cars miles away. They were also able to manipulate a Jeep's stereo, wipers and even turn off the vehicles engine while it was on the highway. The manufacturer later fixed this vulnerability, but in-car hacks still proved possible.
Hacking cars over the internet could be devastating.
There are a dozen manufacturer telematic systems that connect vehicles to the internet such as Chrysler's Uconnect, GM's Onstar, Infiniti's Connection and Hyundai's Bluelink. How long until we see a malicious hack, such as one where a disgruntled employee "bricked" nearly 100 connected cars. Or hacks that infiltrate our vehicles through our smartphones as proven possible earlier this year.
If hacks similar to what Miller and Valasek carried out prove repeatable in the wild, a malicious hacker could disable engines on vehicles from miles away. The devastation this would cause doesn't need to be spelled out.
Protecting us from us

Sadly, the proliferation of connected, or Internet of Things (IoT), devices and the potential for harm has seemed to outpace our efforts to establish measures for accountability. Groups such as I am the Calvary, co-founded by Josh Gorman, hope to protect IoT devices like automobiles and medical devices from attacks. Legislation has also been presented to help curtail possible abuses of IoT vulnerabilities.
Connected devices, riding the message of convenience, are pushing deeper and more broadly into our lives. Refrigerators, stoves, microwaves, cars, and more are joining the ranks of phones, TVs, PCs, cameras and wearables as an all-engulfing army of always-connected devices conveying our personal data across the internet.
Not long ago Vizio was charged with spying on customers via Smart TVs and the CIA allegedly hacked Samsung TVs to surreptitiously spy on targets. As more devices with more cameras, more microphones and more access to our personal data are positioned more broadly around us, more access points into our lives are being positioned as well.
Nowhere to hide...

As IoT devices permeate the public sphere supported by an intelligent cloud passing our data across devices to support the mobility of our experiences, even greater opportunities for exposure are presented.
Dystopian abuse of Microsoft's AI driven camera tech is inevitable
Security professionals have shared a lot of home security system data is routed through China for cost reasons for instance. Hackers, therefore, can come in the form of rogue individuals, organizations or even governments.
As we allow more of the internet into our lives via our phones, homes, automobiles and more we should seriously consider who else we may be letting in.

Jason L Ward is a Former Columnist at Windows Central. He provided a unique big picture analysis of the complex world of Microsoft. Jason takes the small clues and gives you an insightful big picture perspective through storytelling that you won't find *anywhere* else. Seriously, this dude thinks outside the box. Follow him on Twitter at @JLTechWord. He's doing the "write" thing!